🧨 The Minecraft Malware Attack That Exposed a Global Supply Chain Vulnerability — And What Developers Must Learn
In 2024, the Minecraft community faced one of its most severe security threats to date. A multi-stage malware campaign known as Fracturiser infected thousands of users through seemingly legitimate mods hosted on trusted platforms like CurseForge and Bukkit. Behind the scenes? A coordinated supply chain attack exploiting developer accounts, modpack distribution, and ecosystem trust.
This deep dive explores how this attack happened, why it’s not isolated, and the tactical, product-level decisions teams must make to protect users—and their own reputations.
The Attack: Fracturiser and the Stargazers Ghost Network
This wasn’t a typical phishing scam or sketchy download. It was a stealthy, modular, multi-stage malware infection delivered through real mod updates. Once activated, the malware:
Downloaded multiple payloads to steal login credentials, cookies, and crypto wallets
Modified `.jar` files on the local system to spread laterally
Persisted between reboots, evading antivirus detection
This operation was part of a broader campaign by the Stargazers Ghost Network, a malware distribution-as-a-service (DaaS) actor that’s been operating since at least 2023.
According to Check Point Research, this group:
Used over 3,000 fake GitHub accounts to spread infostealers
Infected 17,000+ systems in late 2024 via a new Godot-based malware variant
Boosted credibility by inflating GitHub stars
Most recently, weaponized Java-based Minecraft mods in a way that bypassed all major antivirus engines
Security Failures in the Modding Ecosystem
❌ Weak Developer Account Protection: Even developers using 2FA had their accounts compromised—likely via session hijacking, token theft, or cookie reuse.
❌ Lack of Artifact Verification: Mods were not cryptographically signed, and mod loaders lacked enforcement mechanisms for integrity verification.
❌ Blind Dependency Inclusion: Modpack builders automatically bundled updated mods without validating upstream changes, opening the door to silent infections.
❌ Poor Runtime Threat Detection: Traditional antivirus software completely missed this threat. It took the community’s custom-built tools (e.g. nekodetector) to surface and neutralize infections.
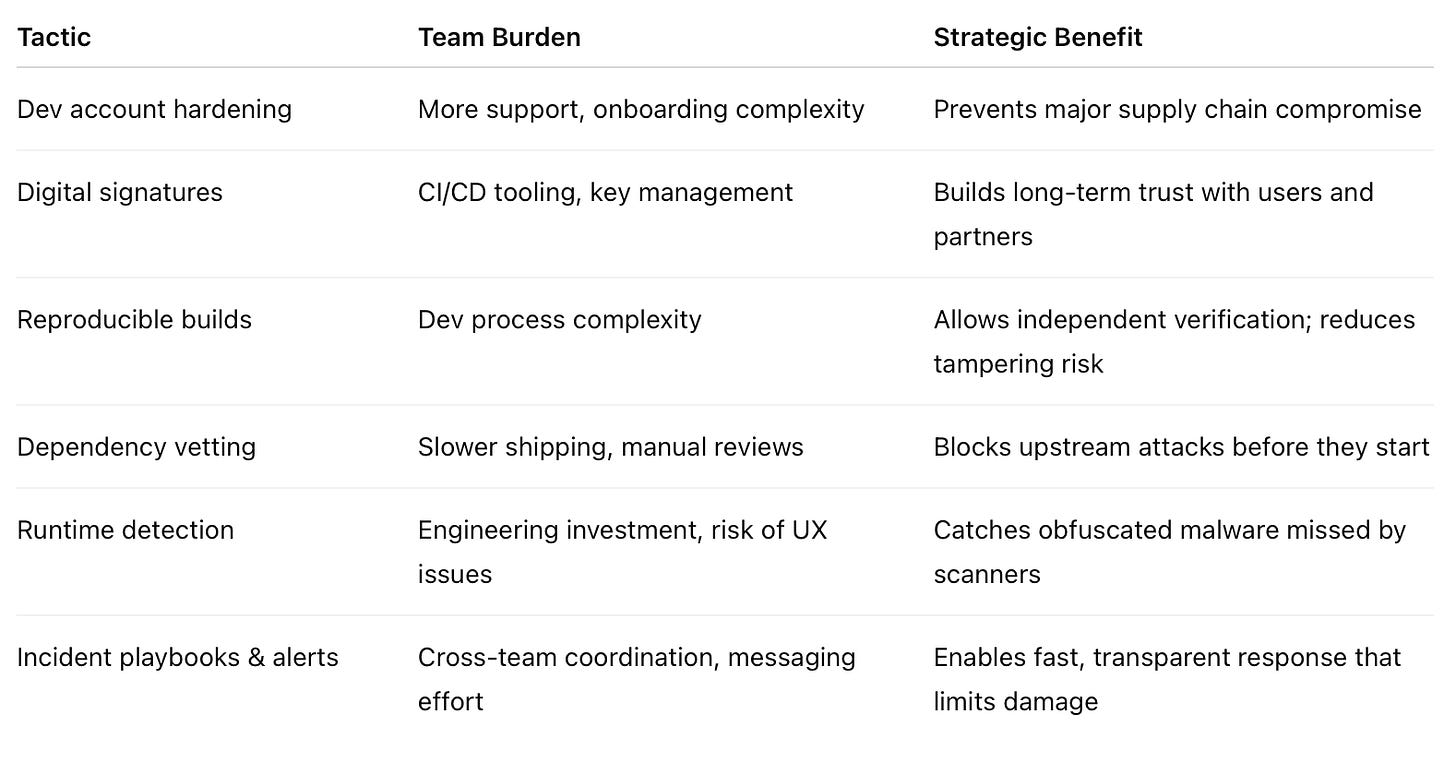
Tactical Actions to Secure Your Ecosystem
If your platform distributes third-party code—mods, plugins, extensions, or libraries—these tactical steps are non-negotiable.
Enforce Strong Developer Authentication
Use hardware security keys (e.g. YubiKey)
Auto-expire tokens and monitor geographic anomalies
Prevent re-use of session cookies
Sign All Published Artifacts
Require cryptographic signatures via Sigstore
Display trust badges or verification levels
Prevent loaders or clients from running unsigned code
Lock and Vet Dependencies
Record version hashes in modpack lockfiles
Block automatic updates from upstream
Scan dependencies for suspicious changes before inclusion
Monitor Behavior at Runtime
Detect reflective loading, clipboard sniffing, and outbound connections
Flag abnormal file writes or class injections
Alert users with mod behavior summaries—not vague warnings
Prepare for Fast Incident Response
Build workflows to revoke compromised releases quickly
Push alerts via launchers, Discord, and web dashboards
Publish clear removal guides and auto-healing scripts
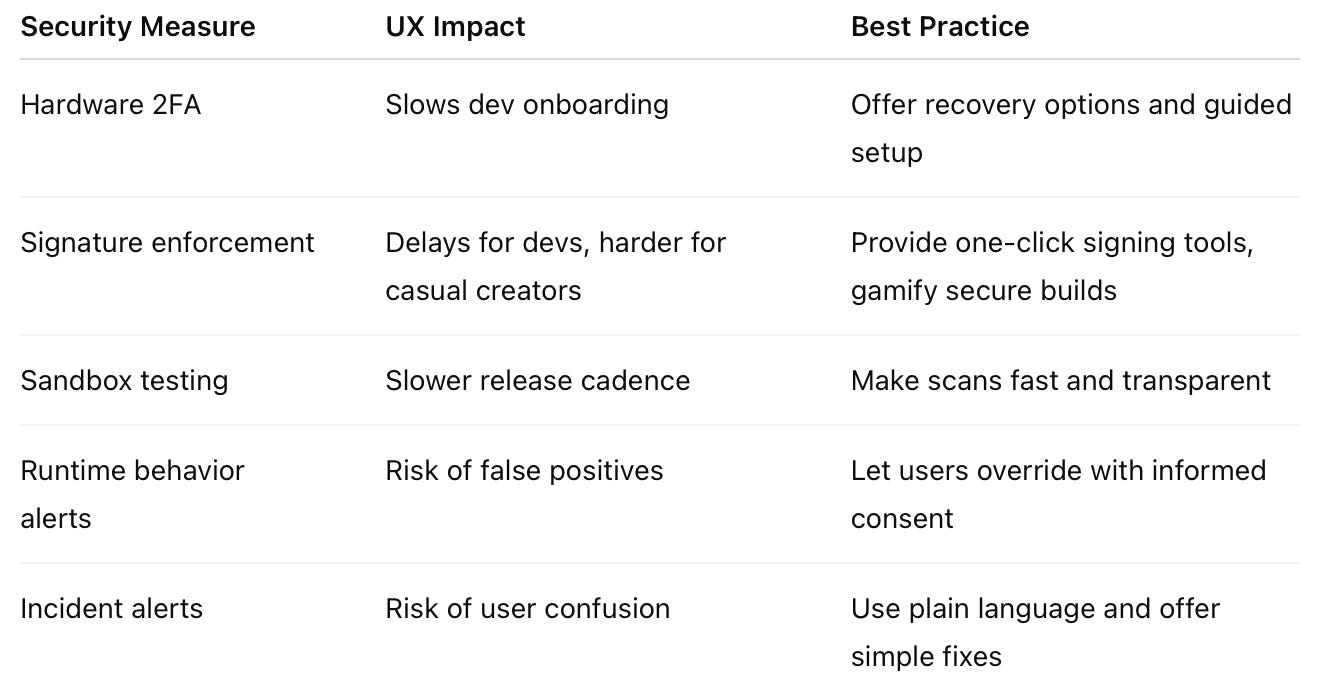
Security Tactics vs. User Experience
These security practices affect more than your backend—they shape how users and developers experience your product. Poorly implemented controls cause friction, pushback, and churn.
Cost-Benefit Matrix for Product Teams
Final Takeaway: Build Security as a Product Feature
This wasn’t just a modding story—it was a supply chain failure, an ecosystem trust collapse, and a developer UX case study rolled into one.
If you're building platforms that depend on:
Modding (Minecraft, Roblox, Skyrim)
Plugins (WordPress, Chrome extensions)
Packages (npm, PyPI, crates.io)
Then you’re already exposed to similar risks. Your users trust that your ecosystem is safe. Your job is to make security invisible—but strong.
PARTNER WITH US
We’re now welcoming a limited number of sponsors who align with our SaaS-focused audience.
👉 Interested? Fill out this quick form to start the conversation.
Feel free to chat for inquires at callmariaph@gmail.com